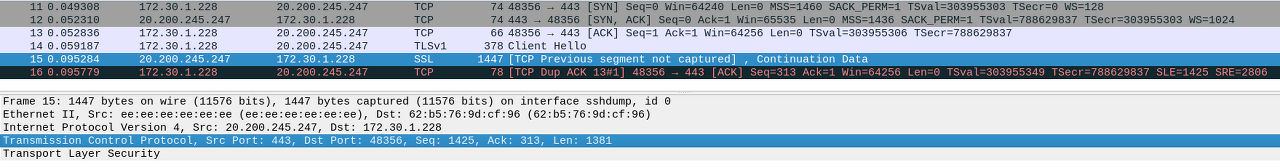
https://jsty.tistory.com/330 There was a problem that could not access github.com in the docker container executed through dockerd(dind) on Kubernetes. All other sites worked for the most part. Connection that work: echo "" | openssl s_client -connect dl-cdn.alpinelinux.org:443 CONNECTED(00000003) depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1 verify return :1 depth=1 C = US, O = Let 's Encrypt, CN = R3 verify return:1 depth=0 CN = dl-cdn.alpinelinux.org verify return:1 --- Certificate chain 0 s:CN = dl-cdn.alpinelinux.org i:C = US, O = Let' s Encrypt, CN = R3 1 s:C = US, O = Let 's Encrypt, CN = R3 i:C = US, O = Internet Security Research Group, CN = ISRG Root X1 2 s:C = US, O = Internet Security Research Group, CN = ISRG Root X1 i:O = Digital Signature Trust Co., CN = DST Root CA X3 --- Server certificate -----BEGIN CERTIFICATE----- ... -----END CERTIFICATE----- subject=CN = dl-cdn.alpinelinux.org issuer=C = US, O = Let&